In the following post I will do some “research” on VPN debugs in Fortigate. It may usefull for those who has basic Foritgate VPN problems or the peer Fortigate has a Problem. Debugging should be usefull for troubleshooting, but should not only be used for troubleshooting. It should be used to understand and see how things really work.
If something wrong it may be too late to understand how things worked before.
Fortigate Firewall1 Configuration:
for the first firewall, that is called firewall1, the really basic configuration will be shown. It is a simple vpn with pre-shared key. The following configurations will be used:
– Interface
– VPN Settings
– Firewall Policy
– Route
firewall1 # show system interface
config system interface
edit "internal"
set vdom "root"
set ip 192.168.10.1 255.255.255.240
set allowaccess ping https
set type physical
next
edit "wan2"
set vdom "root"
set allowaccess ping
set type physical
next
edit "wan1"
set vdom "root"
set ip 6.6.6.2 255.255.255.0
set allowaccess ping https ssh
set type physical
next
edit "modem"
next
edit "ssl.root"
set vdom "root"
set type tunnel
next
edit "firewall2"
set vdom "root"
set type tunnel
set interface "wan1"
next
end
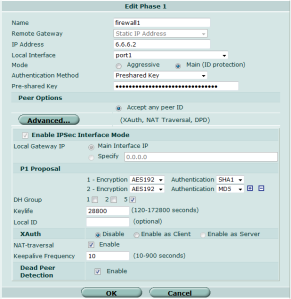
firewall1 # show vpn ipsec phase1-interface
config vpn ipsec phase1-interface
edit "firewall2"
set interface "wan1"
set dpd enable
set nattraversal enable
set proposal aes128-sha1 aes128-md5
set remote-gw 3.3.3.1
set psksecret ENC ECcAADE...
next
end
firewall1 # show vpn ipsec phase2-interface
config vpn ipsec phase2-interface
edit "firewall2-ph2"
set pfs enable
set phase1name "firewall2"
set proposal aes192-sha1 aes192-md5
set replay enable
set src-subnet 192.168.10.0 255.255.255.240
next
end
firewall1 # show firewall policy
config firewall policy
edit 1
set srcintf "internal"
set dstintf "firewall2"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ANY"
next
end
firewall1 # show router static
config router static
edit 1
set device "wan1"
set dst 6.0.0.0 255.0.0.0
set gateway 6.6.6.1
next
edit 2
set device "firewall2"
set distance 5
next
edit 3
set device "wan1"
set dst 3.3.3.1 255.255.255.255
set gateway 6.6.6.1
next
end
|
Fortigate Firewall2 only VPN Configuration:
For the GUI fans, but only the VPN configuration
Manually initiate the IPSEC tunnel:
Normally it should be started automatically, but we can start it manually:
diag vpn tunnel up firewall2-ph2 firewall2 |
Debug commands:
diagnose debug console timestamp enable diagnose debug enable diagnose debug application ike -1 |
To stop it issue the following command:
diagnose debug application ike 0 diagnose debug disable |
DPD Detection debug:
Dead peer detection checks continuously if the peer is reachable, it send a so called ARE-YOU-THERE packets and if the peer supports it it send back an ACKnowledge Packet.
We can see a sequence number in the debug for DPD.
2012-03-21 23:55:48 0:firewall2: link is idle 5 6.6.6.2->3.3.3.1:500 dpd=2 seqno=140c 2012-03-21 23:55:48 0:firewall2: send DPD probe, seqno 5132 2012-03-21 23:55:48 0:firewall2:256: sent IKE msg (R-U-THERE): 6.6.6.2:500->3.3.3.1:500, len=92 2012-03-21 23:55:48 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-21 23:55:48 0: exchange=Informational id=161bed44960a86d3/30fb218d646769fa:9ef2e05e len=92 2012-03-21 23:55:48 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-21 23:55:48 0:firewall2:256: notify msg received: R-U-THERE-ACK 2012-03-21 23:55:53 0:firewall2: link is idle 5 6.6.6.2->3.3.3.1:500 dpd=2 seqno=140d 2012-03-21 23:55:53 0:firewall2: send DPD probe, seqno 5133 2012-03-21 23:55:53 0:firewall2:256: sent IKE msg (R-U-THERE): 6.6.6.2:500->3.3.3.1:500, len=92 2012-03-21 23:55:53 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-21 23:55:53 0: exchange=Informational id=161bed44960a86d3/30fb218d646769fa:fcb630e9 len=92 2012-03-21 23:55:53 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-21 23:55:53 0:firewall2:256: notify msg received: R-U-THERE-ACK |
VPN disconnect debug – initiated from peer:
The disconnect was initiated from the other peer.
2012-03-22 00:13:09 0:firewall2:256: recv IPsec SA delete, spi count 1
2012-03-22 00:13:09 0:firewall2: deleting SA with SPI 2a08e9b4
2012-03-22 00:13:09 0:firewall2: deleted SA with SPI 2a08e9b4, firewall2-ph2 has 0 SAs left
2012-03-22 00:13:09 0:firewall2: sending SNMP tunnel DOWN trap for firewall2-ph2
2012-03-22 00:13:09 0:firewall2: found phase2 firewall2-ph2
2012-03-22 00:13:09 0:firewall2:256: send IPsec SA delete, spi 69c76327
2012-03-22 00:13:09 0:firewall2:256: sent IKE msg (IPsec SA_DELETE-NOTIFY): 6.6.6.2:500->3.3.3.1:500, len=76
2012-03-22 00:13:09 0:firewall2:256: recv ISAKMP SA delete 161bed44960a86d3/30fb218d646769fa
2012-03-22 00:13:09 0:firewall2: deleting
2012-03-22 00:13:09 0:firewall2: flushing
2012-03-22 00:13:09 0:firewall2: flushed
2012-03-22 00:13:09 0:firewall2: deleted
|
VPN Initiation timesout debug, VPN peer does not reply:
DPD is still active, the other peer does not reply to vpn session creation.
2012-03-22 00:30:43 0:firewall2: created DPD triggered connection: 0x8c1f8e8 5 6.6.6.2->3.3.3.1:500. 2012-03-22 00:30:43 0:firewall2: new connection. 2012-03-22 00:30:43 0:firewall2:327: initiator: main mode is sending 1st message... 2012-03-22 00:30:43 0:firewall2:327: cookie 590262b9951dc2b8/0000000000000000 2012-03-22 00:30:43 0:firewall2:327: sent IKE msg (ident_i1send): 6.6.6.2:500->3.3.3.1:500, len=360 2012-03-22 00:30:43 firewall2: Initiator: sent 3.3.3.1 main mode message #1 (OK) 2012-03-22 00:30:45 0:firewall2:327: sent IKE msg (P1_RETRANSMIT): 6.6.6.2:500->3.3.3.1:500, len=360 2012-03-22 00:30:48 0:firewall2: link fail 5 6.6.6.2->3.3.3.1:500 dpd=2 2012-03-22 00:30:48 0:firewall2: ignore link fail, too old 2012-03-22 00:30:49 0:firewall2:327: sent IKE msg (P1_RETRANSMIT): 6.6.6.2:500->3.3.3.1:500, len=360 2012-03-22 00:30:53 0:firewall2: link fail 5 6.6.6.2->3.3.3.1:500 dpd=2 2012-03-22 00:30:53 0:firewall2: ignore link fail, too old 2012-03-22 00:30:57 0:firewall2:327: sent IKE msg (P1_RETRANSMIT): 6.6.6.2:500->3.3.3.1:500, len=360 2012-03-22 00:30:58 0:firewall2: link fail 5 6.6.6.2->3.3.3.1:500 dpd=2 2012-03-22 00:30:58 0:firewall2: DPD fail 5 6.6.6.2->3.3.3.1:500 send failure, resetting ... 2012-03-22 00:30:58 0:firewall2: deleting 2012-03-22 00:30:58 0:firewall2: flushing 2012-03-22 00:30:58 0:firewall2: flushed 2012-03-22 00:30:58 0:firewall2: deleted |
VPN session creation debug:
What you can see in debug, what the peers discuss in the background:
– DPD detection
– NAT Travelsal ist activated, but NAT is not detected.
– Encryption method (Which AES is not clear from debug.)
– Authentication method is Pre-shared key.
– SA lifetimes
– Authentication succeeded
– Encryption domain from initiator and from responder (This must match)
2012-03-22 12:24:33 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:24:33 0:firewall2:2: initiator: main mode get 1st response... 2012-03-22 12:24:33 0:firewall2:2: VID RFC 3947 2012-03-22 12:24:33 0:firewall2:2: VID DPD 2012-03-22 12:24:33 0:firewall2:2: DPD negotiated 2012-03-22 12:24:33 0:firewall2:2: selected NAT-T version: RFC 3947 2012-03-22 12:24:33 0:firewall2:2: negotiation result 2012-03-22 12:24:33 0:firewall2:2: proposal id = 1: 2012-03-22 12:24:33 0:firewall2:2: protocol id = ISAKMP: 2012-03-22 12:24:33 0:firewall2:2: trans_id = KEY_IKE. 2012-03-22 12:24:33 0:firewall2:2: encapsulation = IKE/none 2012-03-22 12:24:33 0:firewall2:2: type=OAKLEY_ENCRYPT_ALG, val=AES_CBC. 2012-03-22 12:24:33 0:firewall2:2: type=OAKLEY_HASH_ALG, val=SHA. 2012-03-22 12:24:33 0:firewall2:2: type=AUTH_METHOD, val=PRESHARED_KEY. 2012-03-22 12:24:33 0:firewall2:2: type=OAKLEY_GROUP, val=1536. 2012-03-22 12:24:33 0:firewall2:2: ISKAMP SA lifetime=28800 2012-03-22 12:24:34 0:firewall2:2: sent IKE msg (ident_i2send): 6.6.6.2:500->3.3.3.1:500, len=292 2012-03-22 12:24:34 firewall2: Initiator: sent 3.3.3.1 main mode message #2 (OK) 2012-03-22 12:24:34 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 12:24:34 0: exchange=Identity Protection id=a2d17a9502e75b2d/d0808883f3ffc95c len=292 2012-03-22 12:24:34 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:24:34 0:firewall2:2: initiator: main mode get 2nd response... 2012-03-22 12:24:34 0:firewall2:2: NAT not detected 2012-03-22 12:24:34 0:firewall2:2: add initial-contact 2012-03-22 12:24:34 0:firewall2:2: sent IKE msg (ident_i3send): 6.6.6.2:500->3.3.3.1:500, len=108 2012-03-22 12:24:34 firewall2: Initiator: sent 3.3.3.1 main mode message #3 (OK) 2012-03-22 12:24:34 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 12:24:34 0: exchange=Identity Protection id=a2d17a9502e75b2d/d0808883f3ffc95c len=76 2012-03-22 12:24:34 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:24:34 0:firewall2:2: initiator: main mode get 3rd response... 2012-03-22 12:24:34 0:firewall2:2: PSK authentication succeeded 2012-03-22 12:24:34 0:firewall2:2: authentication OK 2012-03-22 12:24:34 firewall2: Initiator: parsed 3.3.3.1 main mode message #3 (DONE) 2012-03-22 12:24:34 0:firewall2:2: ISAKMP SA established 2012-03-22 12:24:34 0:firewall2:2: no pending Quick-Mode negotiations 2012-03-22 12:24:34 2012-03-22 12:24:35 0:firewall2:firewall2-ph2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500, natt_mode=0 2012-03-22 12:24:35 0:firewall2: using existing connection, dpd_fail=0 2012-03-22 12:24:35 0:firewall2: found phase2 firewall2-ph2 2012-03-22 12:24:35 0:firewall2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500 negotiating 2012-03-22 12:24:35 0:firewall2:2: cookie a2d17a9502e75b2d/d0808883f3ffc95c:b3cc0a48 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: initiator selectors 0 192.168.10.0/255.255.255.240:0->0.0.0.0/0.0.0.0:0 2012-03-22 12:24:36 0:firewall2:2: sent IKE msg (quick_i1send): 6.6.6.2:500->3.3.3.1:500, len=396 2012-03-22 12:24:36 firewall2: Initiator: sent 3.3.3.1 quick mode message #1 (OK) 2012-03-22 12:24:36 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 12:24:36 0: exchange=Quick id=a2d17a9502e75b2d/d0808883f3ffc95c:b3cc0a48 len=364 2012-03-22 12:24:36 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: responder selectors 0 192.168.10.0/255.255.255.240:0->0.0.0.0/0.0.0.0:0 2012-03-22 12:24:36 0:firewall2:2: sent IKE msg (quick_i2send): 6.6.6.2:500->3.3.3.1:500, len=60 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: replay protection enabled 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: set sa life soft seconds=1748. 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: set sa life hard seconds=1800. 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: add SA #src=1 #dst=1 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: src 0 4 192.168.10.0/255.255.255.240 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: dst 0 4 0.0.0.0/0.0.0.0 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: installed SA: SPIs=a88bfa10/2a08ea33 2012-03-22 12:24:36 0:firewall2:2:firewall2-ph2:1: sending SNMP tunnel UP trap 2012-03-22 12:24:36 firewall2: Initiator: sent 3.3.3.1 quick mode message #2 (DONE) |
VPN session creation debug (with quick mode):
2012-03-22 02:52:39 0: exchange=Quick id=62edcb0e075bcda4/136dc3418fe9f51e:f282fc5d len=396 2012-03-22 02:52:39 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 02:52:39 0:firewall2:361::7146: responder received first quick-mode message 2012-03-22 02:52:39 0:firewall2:361:7146: peer proposal is: peer:0.0.0.0-255.255.255.255, me:192.168.10.0-192.168.10.15, ports=0/0, protocol=0/0 2012-03-22 02:52:39 0:firewall2:361:7146: trying firewall2-ph2 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: matched phase2 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: autokey 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: negotiation result 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: proposal id = 1: 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: protocol id = IPSEC_ESP: 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: trans_id = ESP_AES (key_len = 192) 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: encapsulation = ENCAPSULATION_MODE_TUNNEL 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: type = AUTH_ALG, val=SHA1 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: set pfs=1536 2012-03-22 02:52:39 0:firewall2:361:firewall2-ph2:7146: using tunnel mode. 2012-03-22 02:52:40 0:firewall2:361: sent IKE msg (quick_r1send): 6.6.6.2:500->3.3.3.1:500, len=364 2012-03-22 02:52:40 firewall2: Responder: sent 3.3.3.1 quick mode message #1 (OK) 2012-03-22 02:52:40 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 02:52:40 0: exchange=Quick id=62edcb0e075bcda4/136dc3418fe9f51e:f282fc5d len=60 2012-03-22 02:52:40 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: replay protection enabled 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: set sa life soft seconds=1753. 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: set sa life hard seconds=1800. 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: add SA #src=1 #dst=1 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: src 0 7 192.168.10.0-192.168.10.15 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: dst 0 7 0.0.0.0-255.255.255.255 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: installed SA: SPIs=69c7632c/2a08ea1b 2012-03-22 02:52:40 0:firewall2:361:firewall2-ph2:7146: sending SNMP tunnel UP trap 2012-03-22 02:52:40 firewall2: Responder: parsed 3.3.3.1 quick mode message #2 (DONE) |
VPN session creation debug (wrong selectors):
The encryption domains or Quick mode selectors do not match between the peers.
This debug is from the initiator:
2012-03-22 12:30:31 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:30:31 0:firewall2:2: initiator: main mode get 1st response... 2012-03-22 12:30:31 0:firewall2:2: VID RFC 3947 2012-03-22 12:30:31 0:firewall2:2: VID DPD 2012-03-22 12:30:31 0:firewall2:2: DPD negotiated 2012-03-22 12:30:31 0:firewall2:2: selected NAT-T version: RFC 3947 2012-03-22 12:30:31 0:firewall2:2: negotiation result 2012-03-22 12:30:31 0:firewall2:2: proposal id = 1: 2012-03-22 12:30:31 0:firewall2:2: protocol id = ISAKMP: 2012-03-22 12:30:31 0:firewall2:2: trans_id = KEY_IKE. 2012-03-22 12:30:31 0:firewall2:2: encapsulation = IKE/none 2012-03-22 12:30:31 0:firewall2:2: type=OAKLEY_ENCRYPT_ALG, val=AES_CBC. 2012-03-22 12:30:31 0:firewall2:2: type=OAKLEY_HASH_ALG, val=SHA. 2012-03-22 12:30:31 0:firewall2:2: type=AUTH_METHOD, val=PRESHARED_KEY. 2012-03-22 12:30:31 0:firewall2:2: type=OAKLEY_GROUP, val=1536. 2012-03-22 12:30:31 0:firewall2:2: ISKAMP SA lifetime=28800 2012-03-22 12:30:31 0:firewall2:2: sent IKE msg (ident_i2send): 6.6.6.2:500->3.3.3.1:500, len=292 2012-03-22 12:30:31 firewall2: Initiator: sent 3.3.3.1 main mode message #2 (OK) 2012-03-22 12:30:32 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 12:30:32 0: exchange=Identity Protection id=e83ab30342b29b82/8e584f50fc268376 len=292 2012-03-22 12:30:32 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:30:32 0:firewall2:2: initiator: main mode get 2nd response... 2012-03-22 12:30:32 0:firewall2:2: NAT not detected 2012-03-22 12:30:32 0:firewall2:2: add initial-contact 2012-03-22 12:30:32 0:firewall2:2: sent IKE msg (ident_i3send): 6.6.6.2:500->3.3.3.1:500, len=108 2012-03-22 12:30:32 firewall2: Initiator: sent 3.3.3.1 main mode message #3 (OK) 2012-03-22 12:30:32 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 12:30:32 0: exchange=Identity Protection id=e83ab30342b29b82/8e584f50fc268376 len=76 2012-03-22 12:30:32 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:30:32 0:firewall2:2: initiator: main mode get 3rd response... 2012-03-22 12:30:32 0:firewall2:2: PSK authentication succeeded 2012-03-22 12:30:32 0:firewall2:2: authentication OK 2012-03-22 12:30:32 firewall2: Initiator: parsed 3.3.3.1 main mode message #3 (DONE) 2012-03-22 12:30:32 0:firewall2:2: ISAKMP SA established 2012-03-22 12:30:32 0:firewall2:2: no pending Quick-Mode negotiations 2012-03-22 12:30:32 2012-03-22 12:30:32 0:firewall2:firewall2-ph2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500, natt_mode=0 2012-03-22 12:30:32 0:firewall2: using existing connection, dpd_fail=0 2012-03-22 12:30:32 0:firewall2: found phase2 firewall2-ph2 2012-03-22 12:30:32 0:firewall2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500 negotiating 2012-03-22 12:30:32 0:firewall2:2: cookie e83ab30342b29b82/8e584f50fc268376:0bc0f9f4 2012-03-22 12:30:32 0:firewall2:2:firewall2-ph2:1: initiator selectors 0 192.168.10.0/255.255.255.240:0->0.0.0.0/0.0.0.0:0 2012-03-22 12:30:32 0:firewall2:2: sent IKE msg (quick_i1send): 6.6.6.2:500->3.3.3.1:500, len=396 2012-03-22 12:30:32 firewall2: Initiator: sent 3.3.3.1 quick mode message #1 (OK) 2012-03-22 12:30:33 0:firewall2:firewall2-ph2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500, natt_mode=0 2012-03-22 12:30:33 0:firewall2: using existing connection, dpd_fail=0 2012-03-22 12:30:33 0:firewall2: found phase2 firewall2-ph2 2012-03-22 12:30:33 0:firewall2:firewall2-ph2:1 ignoring duplicate quick-mode request 2012-03-22 12:30:34 0:firewall2:2: sent IKE msg (P2_RETRANSMIT): 6.6.6.2:500->3.3.3.1:500, len=396 2012-03-22 12:30:35 0:firewall2:firewall2-ph2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500, natt_mode=0 2012-03-22 12:30:35 0:firewall2: using existing connection, dpd_fail=0 2012-03-22 12:30:35 0:firewall2: found phase2 firewall2-ph2 2012-03-22 12:30:35 0:firewall2:firewall2-ph2:1 ignoring duplicate quick-mode request 2012-03-22 12:30:36 0:firewall2:firewall2-ph2: IPsec SA connect 5 6.6.6.2->3.3.3.1:500, natt_mode=0 2012-03-22 12:30:36 0:firewall2: using existing connection, dpd_fail=0 2012-03-22 12:30:36 0:firewall2: found phase2 firewall2-ph2 2012-03-22 12:30:36 0:firewall2:firewall2-ph2:1 ignoring duplicate quick-mode request |
If we initiate on the other side, we can see the what the other peer has:
If we initiate on our side, we wont see what the other peer has. It is worth to test initialisation from the other side:
2012-03-22 12:37:24 0:firewall2:3::90: responder received first quick-mode message 2012-03-22 12:37:24 0:firewall2:3:90: peer proposal is: peer:0.0.0.0-255.255.255.255, me:192.168.11.0-192.168.11.15, ports=0/0, protocol=0/0 2012-03-22 12:37:24 0:firewall2:3:90: trying firewall2-ph2 2012-03-22 12:37:24 0:firewall2:3:90: specified selectors mismatch firewall2: - remote: type=7/7, ports=0/0, protocol=0/0 2012-03-22 12:37:24 0:firewall2:3:90: local=192.168.11.0-192.168.11.15, remote=0.0.0.0-255.255.255.255 2012-03-22 12:37:24 0:firewall2:3:90: - mine: type=7/7, ports=0/0, protocol=0/0 2012-03-22 12:37:24 0:firewall2:90: local=192.168.10.0-192.168.10.15, remote=0.0.0.0-255.255.255.255 2012-03-22 12:37:24 0:firewall2:3:90: no matching phase2 found 2012-03-22 12:37:24 0:firewall2:3::90: failed to get responder proposal 2012-03-22 12:37:24 firewall2: Responder: parsed 3.3.3.1 quick mode message #1 (ERROR) 2012-03-22 12:37:24 0:firewall2:3: error processing quick-mode msg from 3.3.3.1 as responder |
Wrong preshared key debug:
Not so talkative to identify pre-shared key problems, the logs are better in this case.
2012-03-22 12:45:51 0: exchange=Identity Protection id=f894aec7b60cd50d/dd68f0cd443b3ff2 len=108 2012-03-22 12:45:51 0:firewall2:22: responder: main mode get 3rd message... 2012-03-22 12:45:51 0:firewall2:22: parse error 2012-03-22 12:45:51 firewall2: Responder: pars2012-03-22 12:45:51 0:firewall2: link fail 5 6.6.6.2->3.3.3.1:500 dpd=2 2012-03-22012-03-22 12:45:51 0:firewall2:21: sent IKE msg (P1_RETRANSMIT): 6.6.6.2:500->3.3.3.1:500, len=292 2012-03-22 12:45:52 0:firewall2:22: sent IKE msg (P1_RETRANSMIT): 6.6.6.2:500->3.3.3.1:500, len=292 2012-03-22 12:45:52 0: comes 3.3.3.1:500->6.6.6.2:500,ifindex=5.... 2012-03-22 12:45:52 0: exchange=Identity Protection id=f894aec7b60cd50d/dd68f0cd443b3ff2 len=108 2012-03-22 12:45:52 0: found firewall2 6.6.6.2 5 -> 3.3.3.1:500 2012-03-22 12:45:52 0:firewall2:22: responder: main mode get 3rd message... 2012-03-22 12:45:52 0:firewall2:22: parse error 2012-03-22 12:45:52 firewall2: Responder: parsed 3.3.3.1 main mode message #3 (ERROR) |

Richard
May 7, 2012
hi,
thanks for this fine compilation of commands.
regards,
Richard
Googs
July 13, 2012
Thanks, very handy
mccs
July 16, 2012
thx indeed
Sylvain
January 24, 2013
Thank you very much for this usefull commands and result compilation, that helped me to fix 2 VPNs.
itsecworks
January 24, 2013
Your welcome :-)
Leandro
February 15, 2013
I’m trying to set up a Client to Site VPN, but I have doubt on how do I have to set up the route for it. I’m doing a route-based VPN with DHCP on it, can you help me out?
itsecworks
February 15, 2013
ööö, for free no way :-) But I have a post on it, have you read that through?
Paste your config to pastebin.com and give me a link.
Leandro
February 18, 2013
Yes I read it, but I couldn’t find what it is missing, I suspect it is a route, because phase 1 completes but the tunnel doesn’t get up.
I’ve sent you my config on the last post.
Sam
April 13, 2013
For posterity… Error -104 means the name of your VPN tunnel is too long. The limit is 15 characters, and as it increments it dies.. ike 0:fClient_VPNlu_1: could not create dialup name fClient_VPNlu_10, too long
Took four TAC tech guys and three days to find the problem.
Ashish.Sawant
July 24, 2013
Hi , though we are using Nat-T , for ipsec vpn in Tunnel mode .
the issue is i am still able to find req on remote-gateway on uDP 500
as it should be on 4500 because Nat-t has been used .
due to this some-time VPN woks & some time not .
can you help in this to resolve the same .
X.X.X.X.500 -> X.X.X.X.500: udp 260
James
January 30, 2014
hi we are trying to use a root certificate on our vpn but we are not able to do so can you help
itsecworks
January 30, 2014
What do you mean with root certificate? Is it a certificate from your root ca?
You may have to create a certificate request with your firewall and let it signed by your root ca and import the signed certificate in your firewall.
That is the general way I have used already.
How could I help?